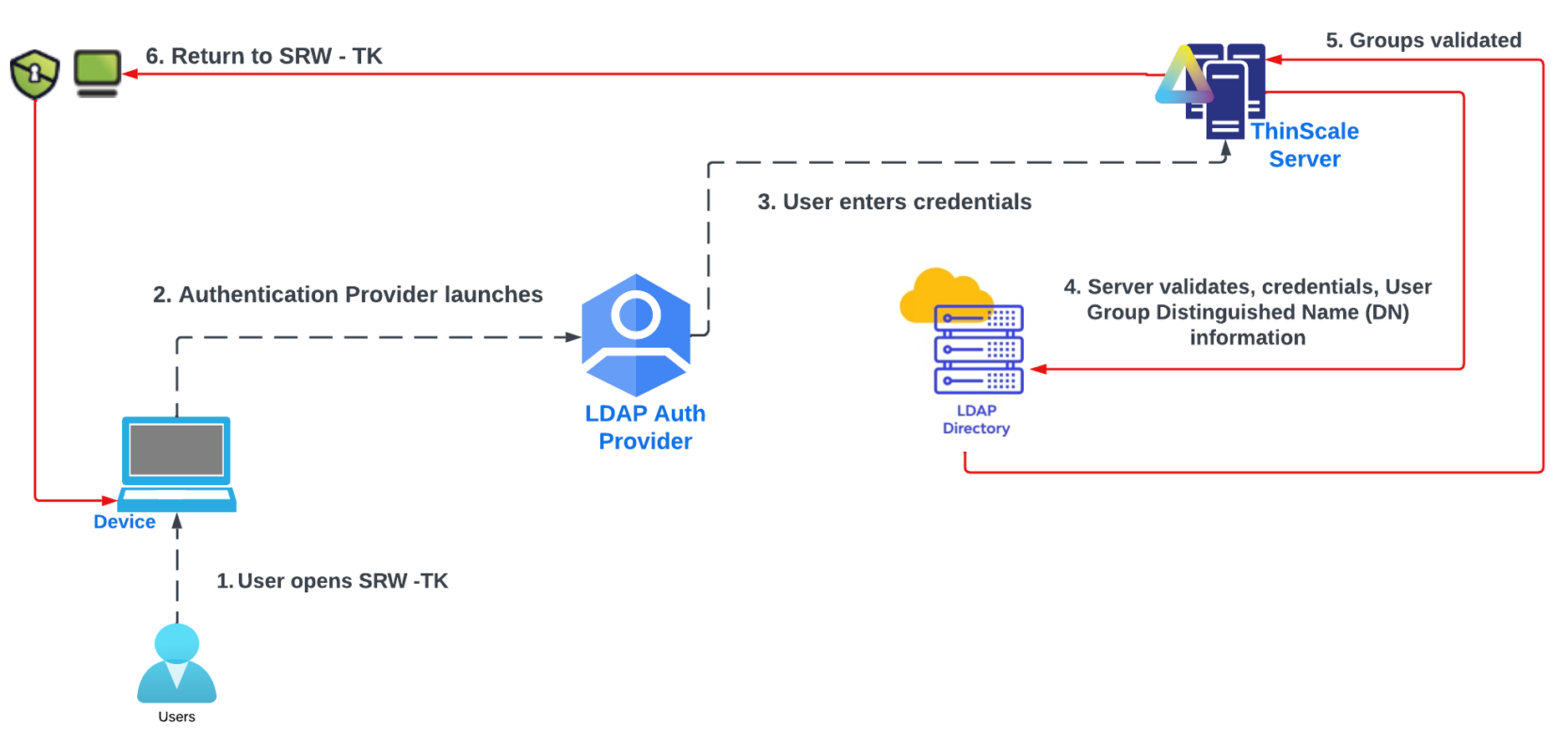
The new Authentication Providers (LDAP, Azure and Ping) will give the administrator the option to authenticate the agent using SRW/TK machines against one of these Identities, prior to launching the application. That way the ThinScale Team has added another layer of security whereas a user has to fully authenticate against an Azure AD or a Ping Authentication in order to fully launch SRW or TK.

Additionally, the admin can use the below option to rename the device which authenticates with one of the below Providers, inside the management console.
Note: rename a device using Ping is currently not supported

Note: ThinScale is not in control of any of the settings in either Azure or Ping. So please talk with your Administrator for more info.
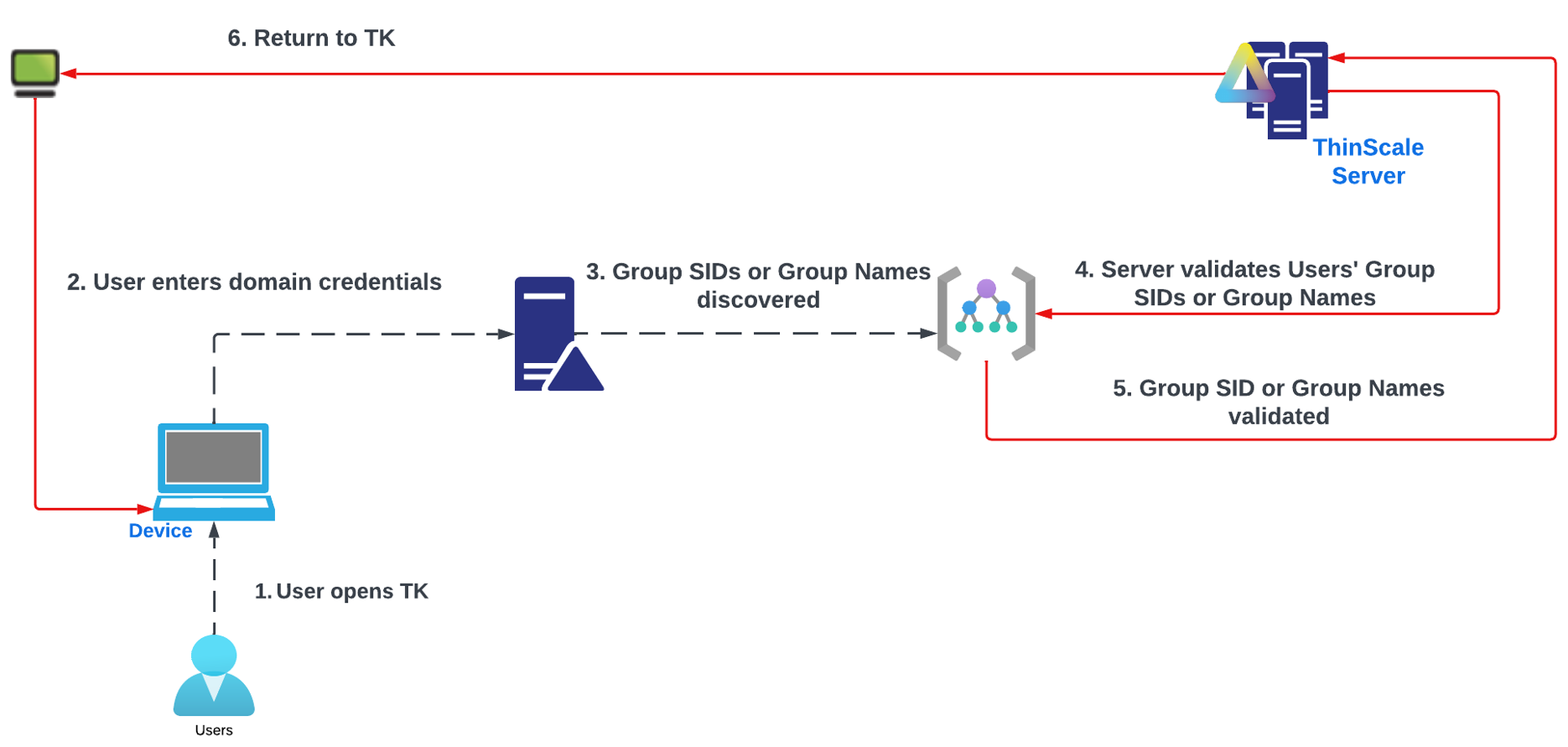
LDAP

Display Name: If enabled the display name is the name that will be displayed on the endpoint. Useful if you want to hide domain name information from the user view.

HostName is the actual domain hostname your user will authenticate against.
LDAP 2
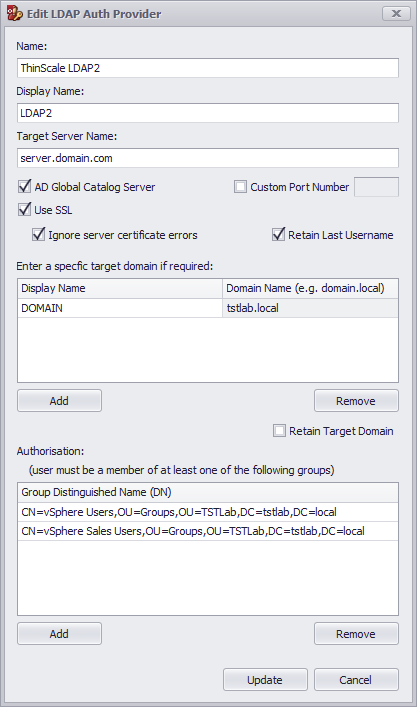
AD Global Catalog Server: The global catalog is a feature of AD domain controllers that allows for a domain controller to provide information on any object in the forest, regardless of whether the object is a member of the domain controller’s domain.
Custom Port Number: The port number that will be used when connecting to the target LDAP server.
Use SSL: if enabled, LDAP/S will be used
Retain Last Username: if enabled, the username typed in the dialog box will be retained
Target Domains: If your target LDAP server has a connection to multiple domains (child domains, forests etc) they can be added as target domains to force authentication to a specific domain.
Display Name: The name displayed in the authentication dialog on the client device.
Domain Name: the domain name that is appended to the username during authentication. (eg. user@domain.com)
Retain Target Domain: if enabled, the last used domain will be retained
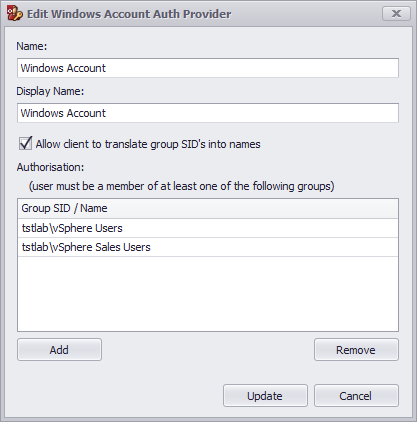
Authorisation: Optionally authorise the user by adding one or more LDAP groups.
If a group is included in the configuration, any authenticating user must be a member of at least of the groups specified in the list to complete the authentication.
--------------------------------------------------------------------------------
Please note:
When AD Global Catolog is enabled please don't use any Custom Port Number.
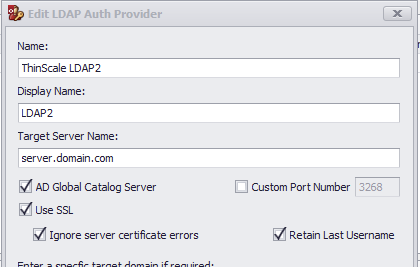
However, if you want to use a custom port then you can simply disable the AD Global Catalog
For normal LDAP with the AD, Global Catolog use port 3268
For LDAPs with the AD, Global Catolog use port 3269
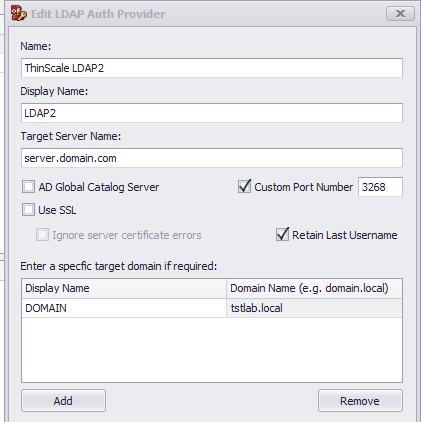
LDAP 2 Flow
Windows Account
Windows Account Flow