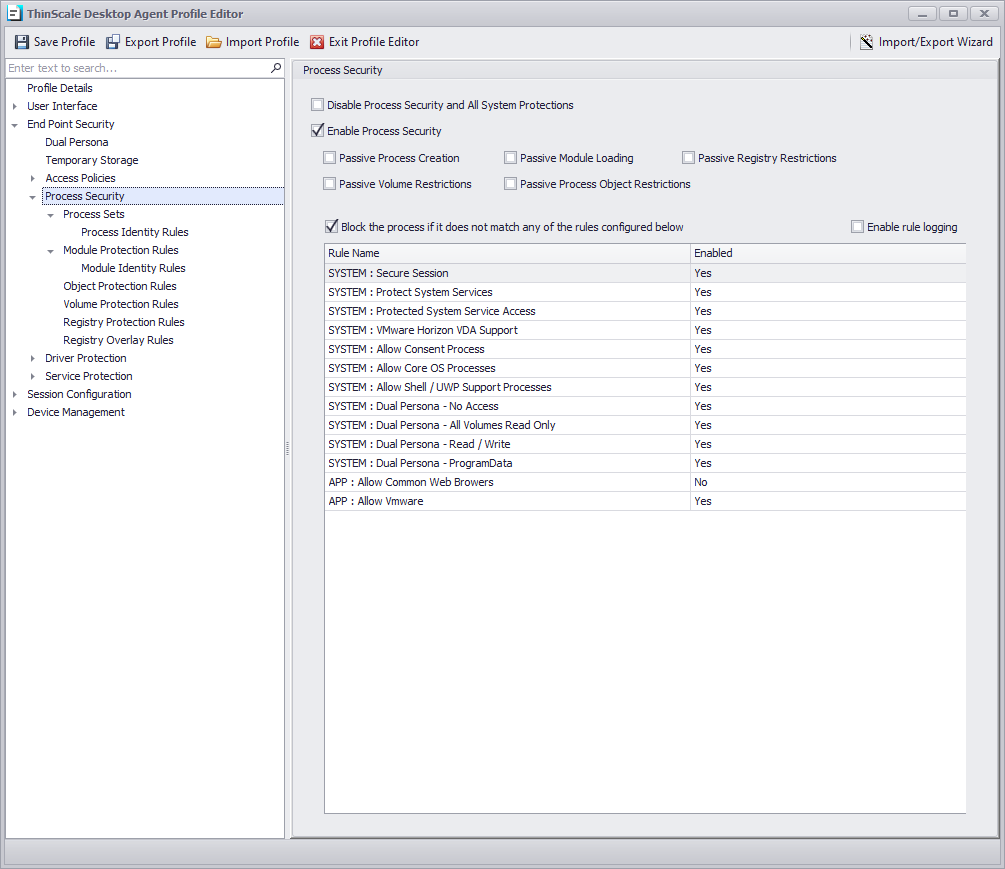
END POINT SECURITY - PROCESS SECURITY
Please Note: Rules may be different from this screen.
CAUTION
Do not alter, amend, or remove SYSTEM rules. Modifying these rules may lead to instability in the TDA session.
Disable Process Security and All System Protections
If enabled, all the default rules applied by the Process Security engine will be disabled. A restart is needed when applied.
Disabling this option is only recommended for troubleshooting.
Enable Process Security
If enabled, any processes added to the list will be allowed/denied execution.
Passive modes
If enabled, any of the Process Security functions (Volume, Module, Registry, etc) will be ignored.
Enable rule logging
If enabled, the administrator can retrieve more information about the application being prevented from executing from the TDA logs file.
Block the executable if it does not match any of the configured rules below
If enabled, and no other rules are created in the list, the console will auto-create a rule for you to prevent incorrect system operation.
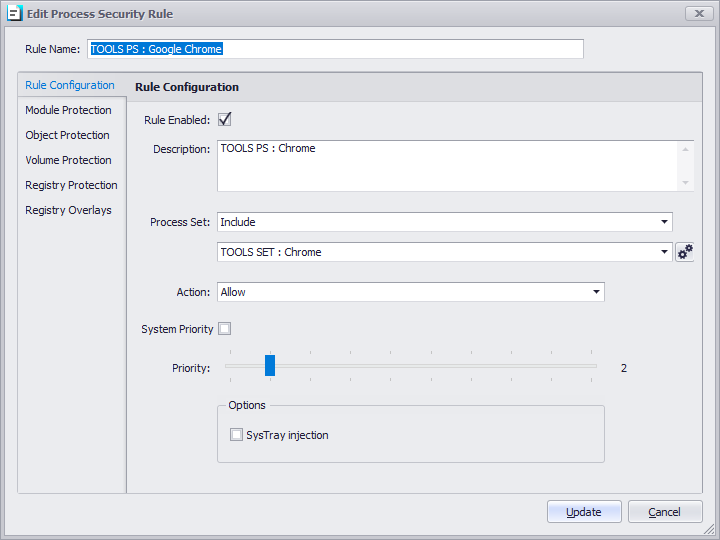
Example: Google Chrome Allowed Rule
Process Sets
A Process Set is a repository where all your process identities (executable name, thumbprints, hashes, and more) are stored.
Action
Specify the desired action (Allow/Block/No Action) to apply to the listed processes.
System Priority
When activated, System Priority takes precedence over a standard priority, even when the latter is configured to a value of 10. A System Priority will mandate the application of a rule ahead of any other rule within the process Set.
Priority
If activated, administrators can assign elevated priority to processes, allowing the engine to prioritize this specific set of rules over others.
Systray Injection
If enabled, the process with the injection enabled can display its icons inside the left button system notification area.
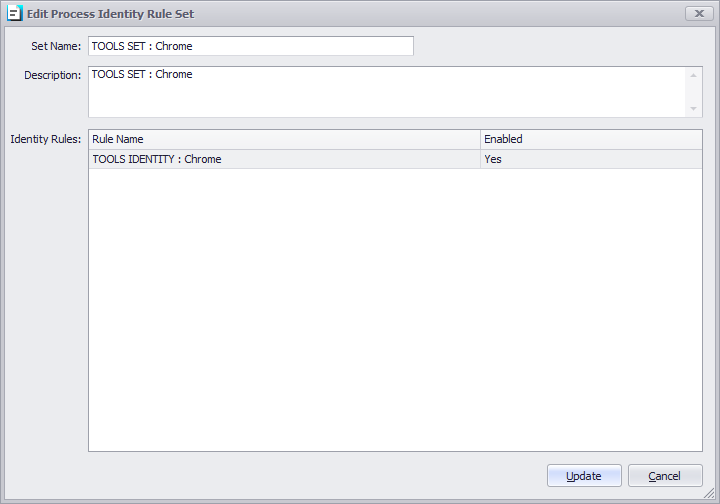
Process Identity (prior v8 known as Application Execution Prevention)
A process Identity entails the configuration by an administrator of criteria determining whether an executable is permitted or denied from execution.
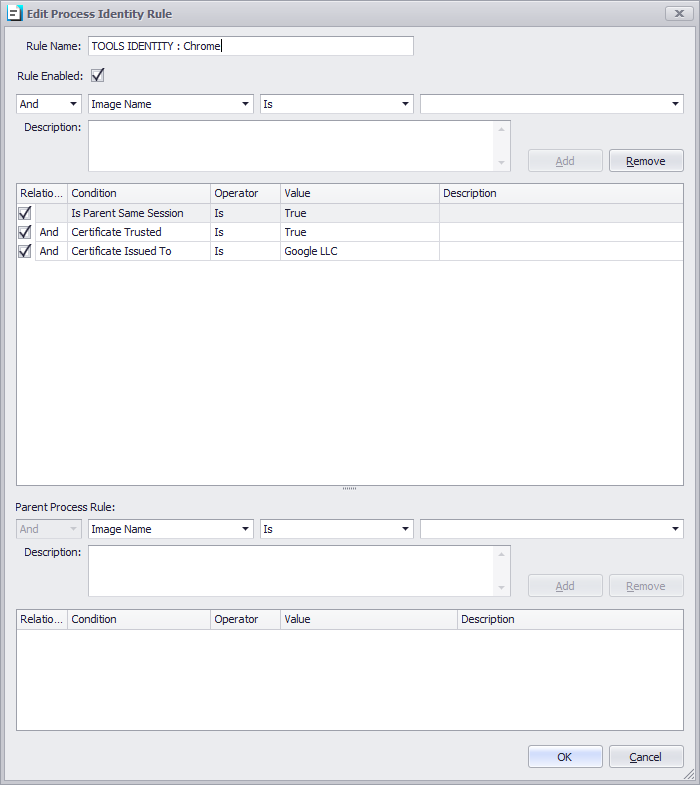
Example: Google Chrome
Rule Name
Describe the name of the rule to be applied.
Action
Select “Allow” or “Deny,” allowing or denying Application execution.
Adding a rule
When creating a rule, there are relationships and conditions you can use to match or not a specific file name, size of the file, last modified date and time, Windows OS binary, and all the other options in the profile editor.
An example of the rule can be seen in the screenshot below. The rule will allow the execution of the locally installed Chrome application.
WARNING:
Process Security is a system-level function preventing a system from operating correctly until the active TDA profile is corrected and reloaded. By default, TDA applications will be allowed once verified by a signed security certificate. Blocking all applications without defined rules will prevent the TDA session from launching correctly.