When deploying FortiClient VPM as Software Package using our Management Console, you will need to add the below configuration to ensure that it runs normally when AEP (v7.5) or Process Security (v8) are enabled.
Please note that the below configuration does not apply to version 7.4 or below.
FortiClient VPN Application
Please follow the below steps to get the application to show inside SRW
Edit your desire SRW Profile
Go to Applications > Local Applications
Right Click > Add > Add Custom Application
Display Name: FortiClient VPN
Command Line: C:\Program Files\Fortinet\FortiClient\FortiClient.exe

Click on Add
Save Profile
Please follow the below steps to get the application to show inside TDA On-Prem
Edit your desired TDA Profile
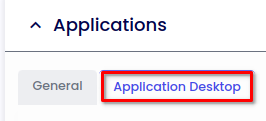
Go to Applications > Application Desktop
Right Click > Add Group > Applications
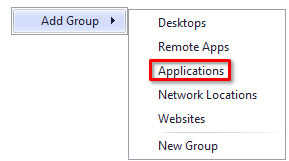
Highlight the Applications group > Right Click > Add Application > Add Custom Application
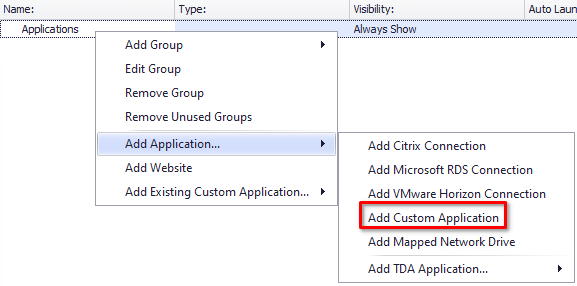
Display Name: FortiClient VPN
Visibility Option: Always Show
Command Line: C:\Program Files\Fortinet\FortiClient\FortiClient.exe
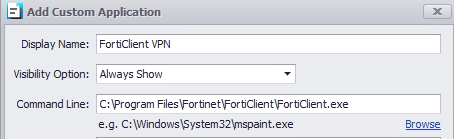
Click on Add
Save Profile
Please follow the below steps to get the application to show inside TDA Cloud
Login to your Device Portal
Navigate to Configuration > UI Profiles
Select your UI Profile > Expand Applications and go to the Application Desktop Tab
Click on the + and Add New Group
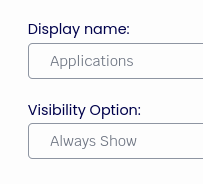
Display Name: Applications
Visibility Option: Always Show
Click Apply
On the right hand side of the Applications Group > click the + to Add New > Add Custom Application

Display Name: FortiClient VPN
Visibility Option: Always Show
Command Line: C:\Program Files\Fortinet\FortiClient\FortiClient.exe

Click Apply
Save the configuration from the top right corner:
AEP Rules for v7.5
Under Application Execution Prevention > Add New Rule
Rule Name: FortiClient VPN
Rule Enabled: Checked
Action: Allow
Certificate Trusted Is: True
AND Certificate Issued To Is: Fortinet Technologies (Canada) ULC
AND Certificate Thumbprint Is: 0F38EA0AA959EA336C743AE18DC9E60A4FD58665

Do not automatically block cross-session processes where no parent rule is set: Checked
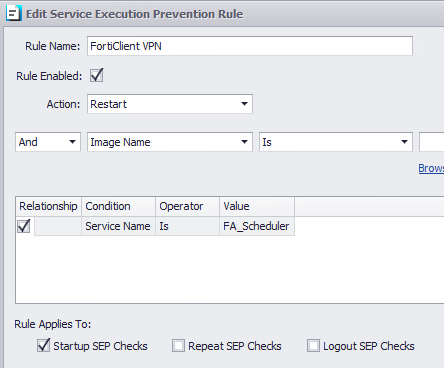
Under Service Execution Prevention > Add New Rule
Rule Name: OpenVPN
Rule Enabled: Checked
Action: Restart
Service Name Is: FA_Scheduler
Rule Applies To: Startup SEP Checks
Click OK
Save Profile
Process Security for v8 On-Prem
Edit your desired TDA Profile
Go to Process Security > Right click on the blank space > Add
Rule Name: SET: FortiClient VPN
Select New Process Set:
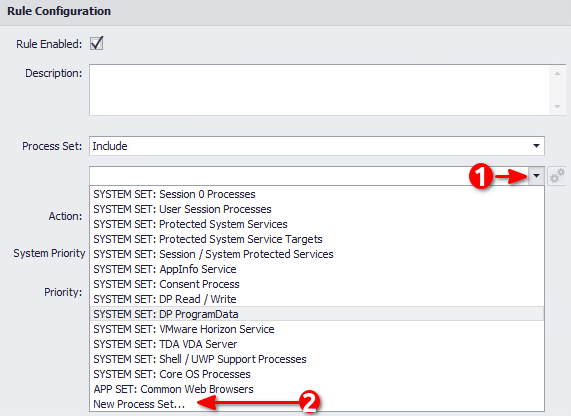
Set Name: SET: FortiClient VPN
Identity Rules > Right Click > Add New
Rule Name: IDENTITY: FortiClient VPN
Certificate Trusted Is: True
AND Certificate Issued To Is: Fortinet Technologies (Canada) ULC
AND Certificate Thumbprint Is: 0F38EA0AA959EA336C743AE18DC9E60A4FD58665

Click on Update
Check that the option for SysTray injection is enabled:

Click Update
Edit SYSTEM: Protected System Service Access
Under Rule Configuration, click on the cog.
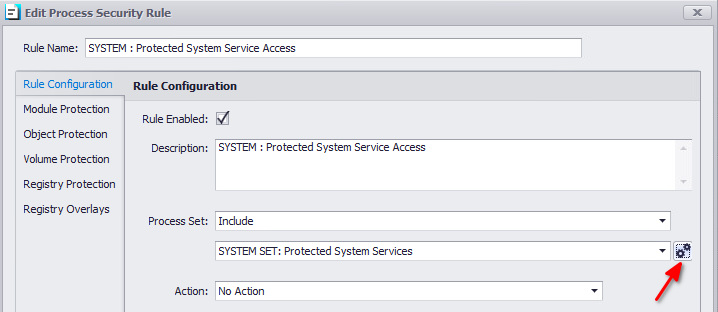
Right Click > Add New
Rule Name: IDENTITY: FortiClient VPN Service
Is Session 0 Is: True
AND Is Service Is: True
AND Certificate Trusted Is: True
AND Certificate Issued To Is: Fortinet Technologies (Canada) ULC
AND Certificate Thumbprint Is: 0F38EA0AA959EA336C743AE18DC9E60A4FD58665
AND Service Name Is: FA_Scheduler
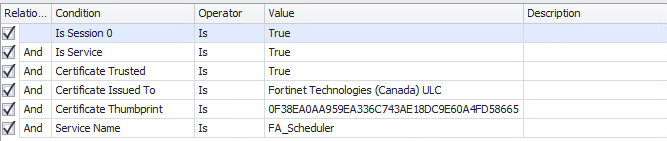
Click OK
Click Update
Under Service Protection
Set Session Start Group to Session Start Actions from the dropdown menu and then click on the cog
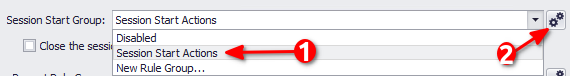
Right Click on the blank space and Add New
Rule Name: Restart FortiClient VPN Service
Rule Enabled: Checked
Action: Restart
Service Name Is: FA_Scheduler
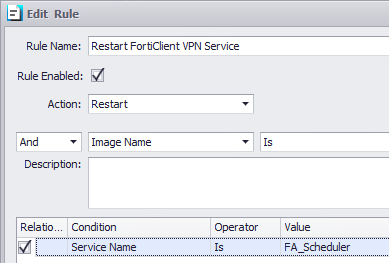
Click OK
Click Update
Save Profile
Process Security for v8 Cloud
Login to your Device Portal
Navigate to Configuration > Security Profiles and open your desired Security Profile
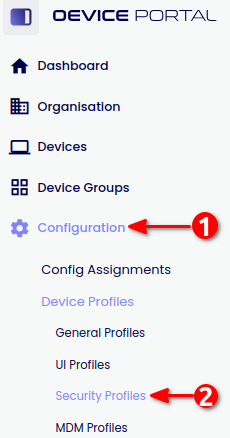
Go to Process Security and expand
Go to Process Security Tab
Click on + Add Item
On the right hand side
Type:
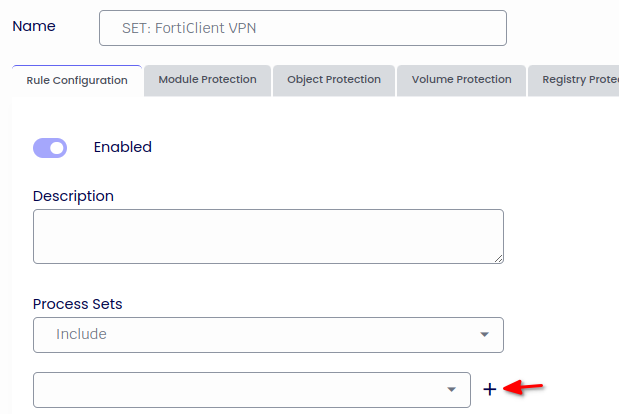
Name: SET: FortiClient VPN
Enabled: Checked
Click on the “+” button
Click on Edit Rules:
Click on + Add Item
Enabled: Checked
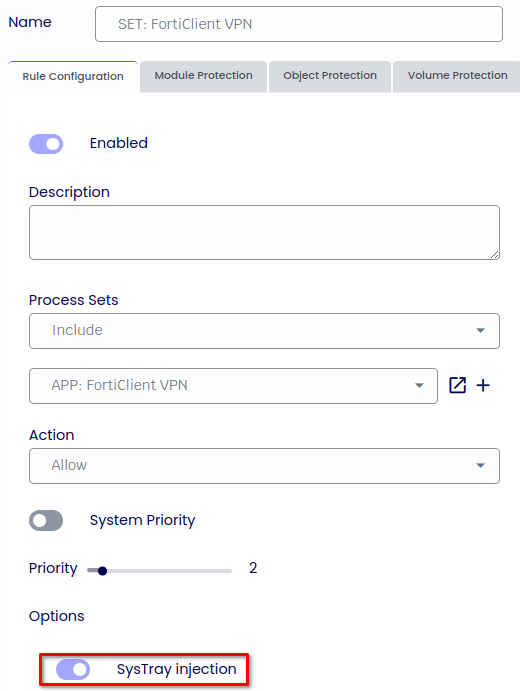
Name: IDENTITY: FortiClient VPN
Certificate Trusted Is: True
AND Certificate Issued To Is: Fortinet Technologies (Canada) ULC
AND Certificate Thumbprint Is: 0F38EA0AA959EA336C743AE18DC9E60A4FD58665

Click Apply
Close popup window
Click Apply and Close the popup window
From the Process Sets dropdown Menu select Include and the new set created
Enable: SysTray Injection
Edit: SYSTEM: Protected System Service Access
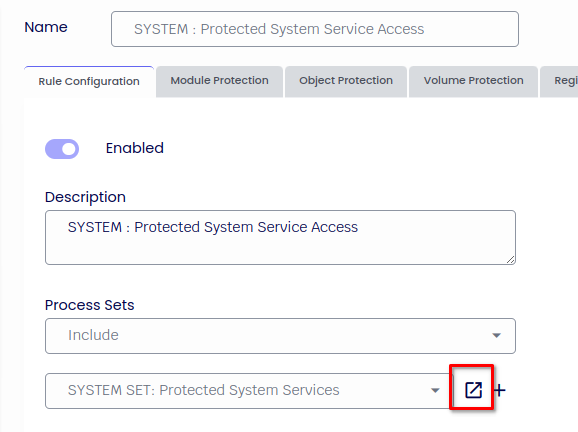
Click on Edit Rules:

Click on + Add Item
Rule Name: APP IDENTITY: FortiClient VPN Service
Is Session 0 Is: True
AND Is Service Is: True
AND Certificate Trusted Is: True
AND Certificate Issued To Is: Fortinet Technologies (Canada) ULC
AND Certificate Thumbprint Is: 0F38EA0AA959EA336C743AE18DC9E60A4FD58665
AND Service Name Is: FA_Scheduler

Go to Service Protection and expand it
Under Session Start Group, edit Session Start Actions
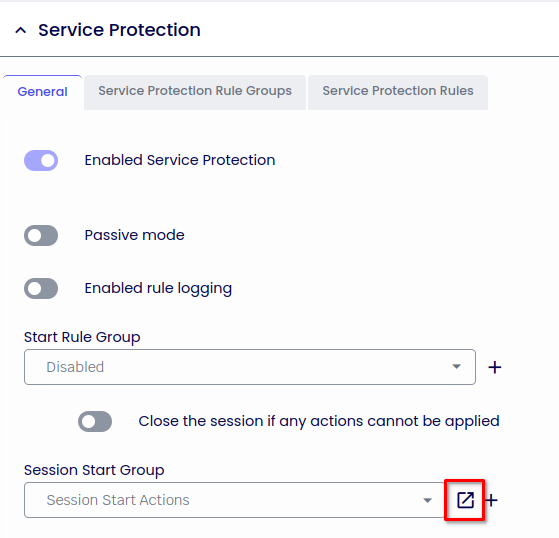
Click on Edit Rules:

Click on + Add Item
Rule Enabled: Checked
Rule Name: Restart FortiClient VPN Service
Action: Restart
Service Name Is: FA_Scheduler
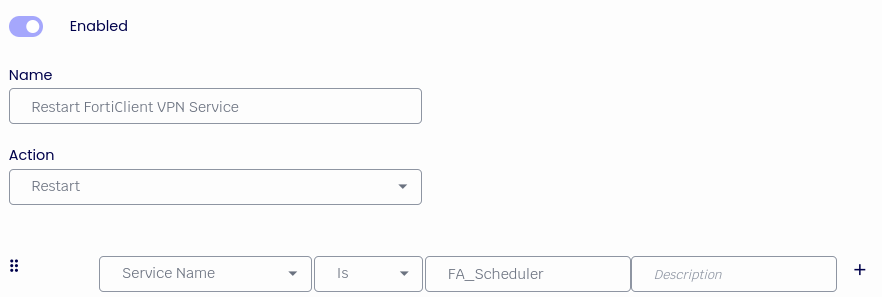
Click Apply
Close popup window
Save the configuration from the top right corner:
