Corporate Device Lockdown
Corporate Device Lockdown Use Case Walkthrough
In implementing our Corporate Device Lockdown quick-start configuration, specific sections within the profile have been modified to establish a baseline secure environment. For further customization and alignment with your organization's specific security policies, please refer to the following resources:
Administrator Guide
Knowledge Base Articles
ThinScale Academy
By leveraging these resources, you can confidently optimize the Corporate Device Lockdown profile to ensure it meets your organization's security needs while providing a seamless user experience for employees utilizing personal devices.
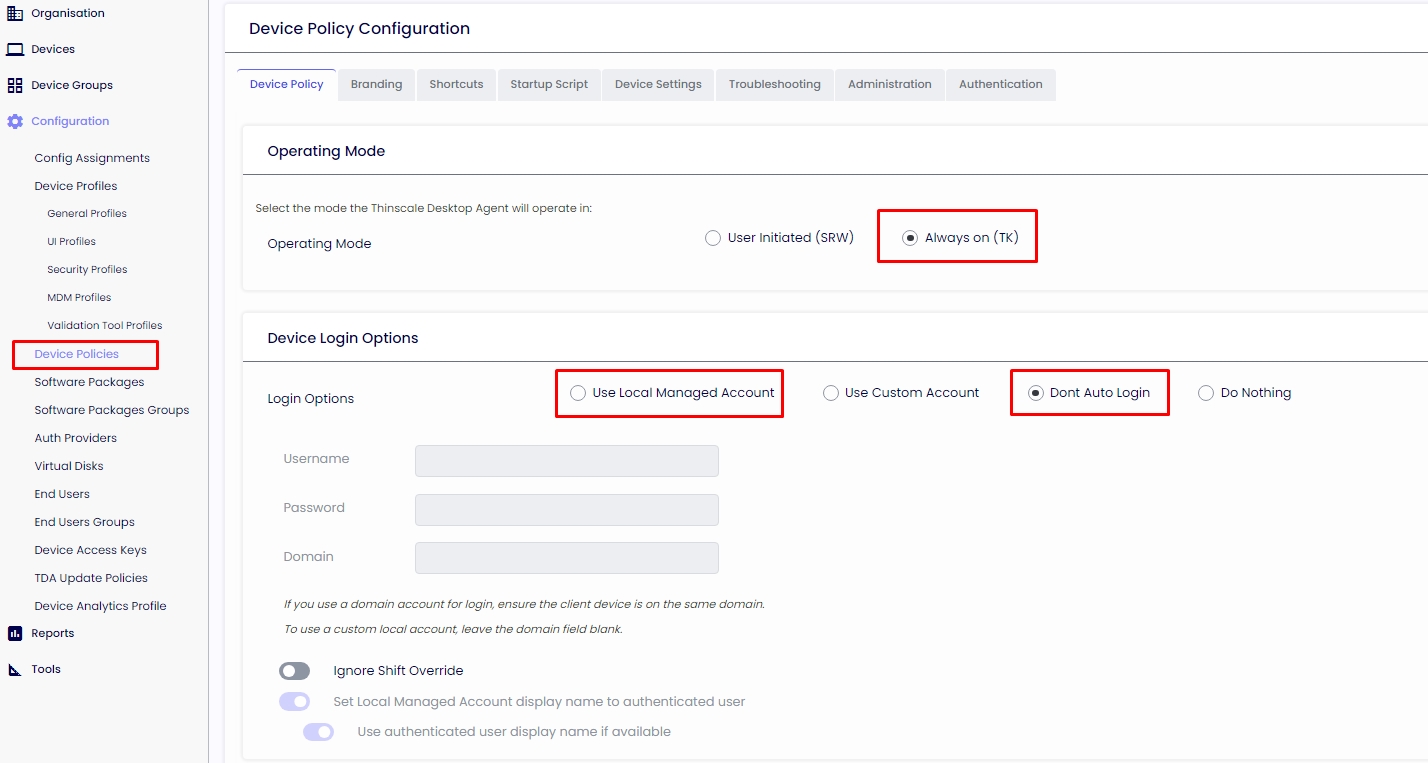
DEVICE POLICIES
The Device Policies are set to the device to operate as Always on (TK).
Use Local Managed Account - This option is used if you want the TDA to have their own Windows user account created without user interaction when the machine starts.
Don't Auto Login - This option is used if you are a domain machine member, and the end-user can enter their credentials on Windows.
Info
Be aware GPO can interfere with TDA policies.
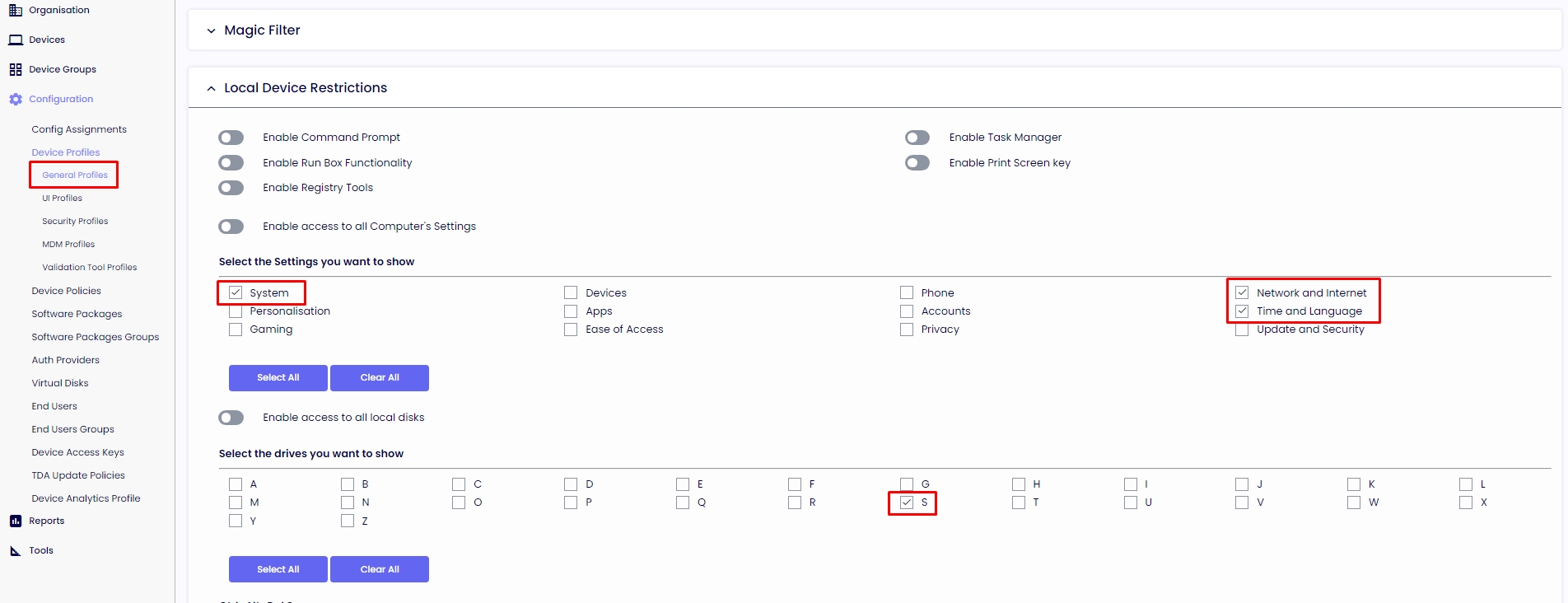
GENERAL PROFILES
In this area, the agent will have only access from the Ribbon Bar to Display, Network, Mouse, and Keyboard settings, and only see the drive letter S from the Dual Persona. All the other drivers on the machine will be fully blocked.
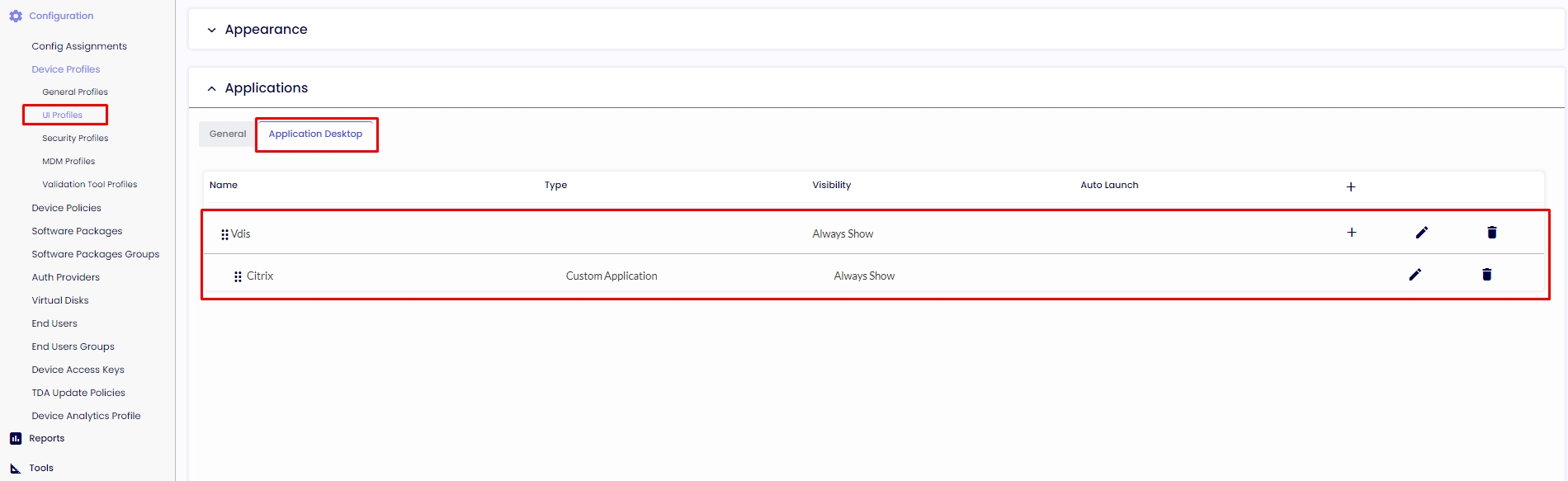
UI PROFILES
In this area, the desktop from the session is used. The applications selected from the quick-start were created here with the shortcut (local path) from where they are installed on the machine.
Our secure browser uses the Webview Framework and only allows websites to be enabled using the URL filtering rules.
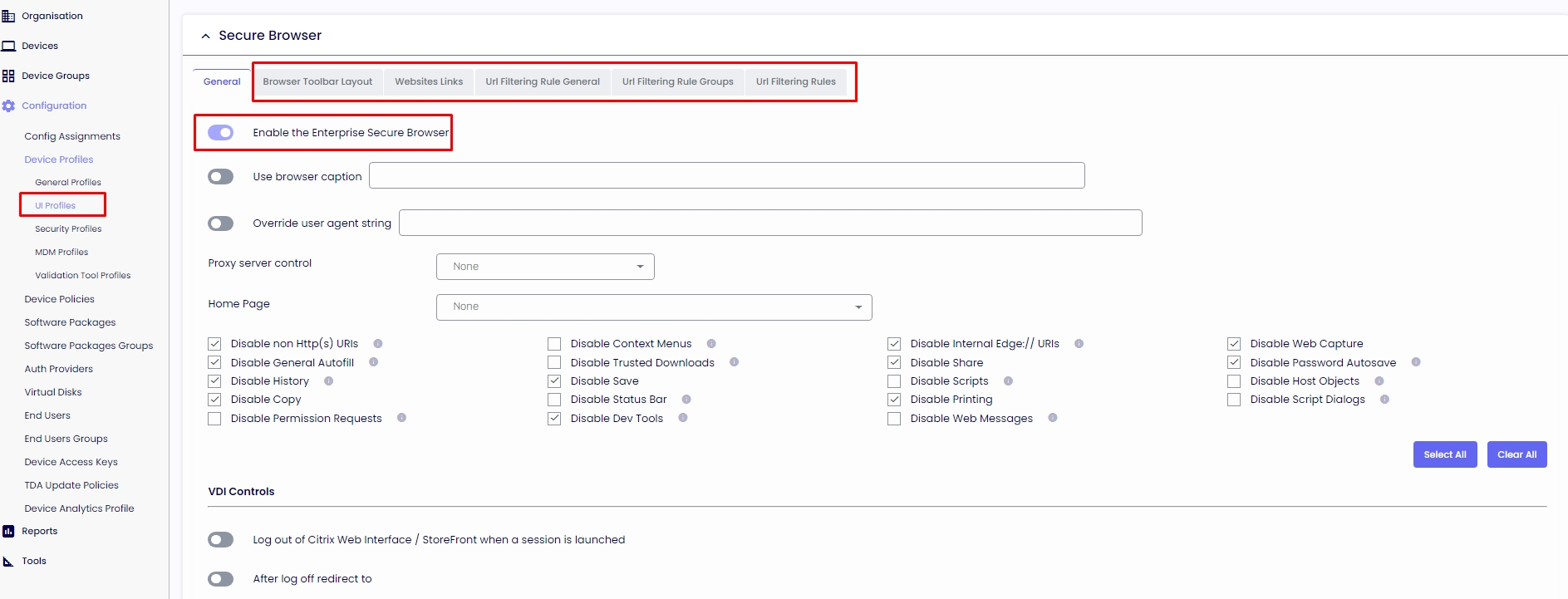
SECURITY PROFILES
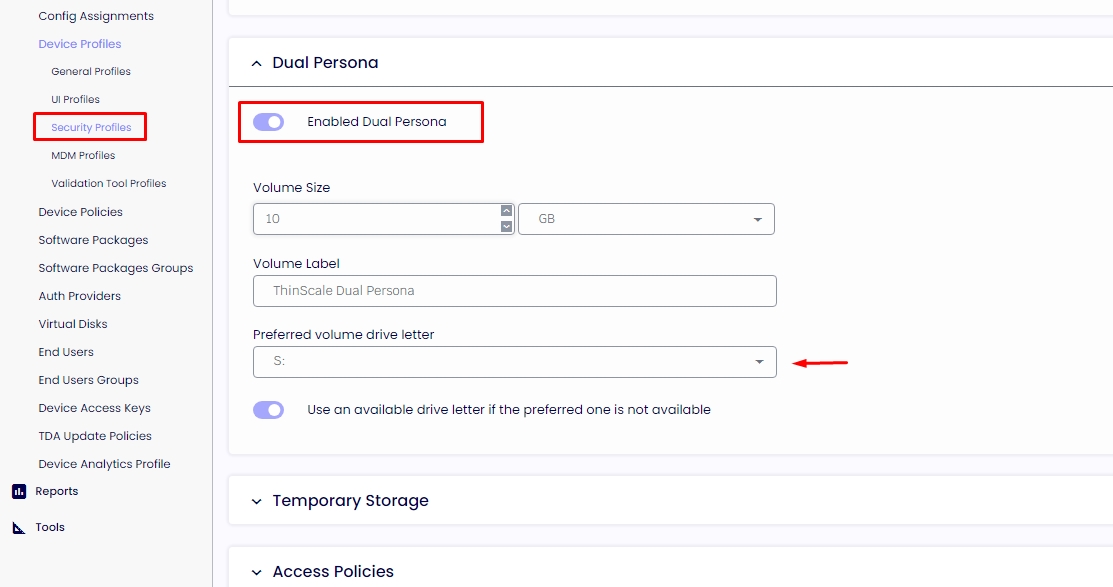
Our Bitlocker encrypted drive is created on the first launch of the TDA, and displayed as volume drive letter S for saving documents and storing the C:\Users\TDA and ProgramData inside of the encrypted drive. This volume drive letter is not available to the agent when he's back to his normal account.
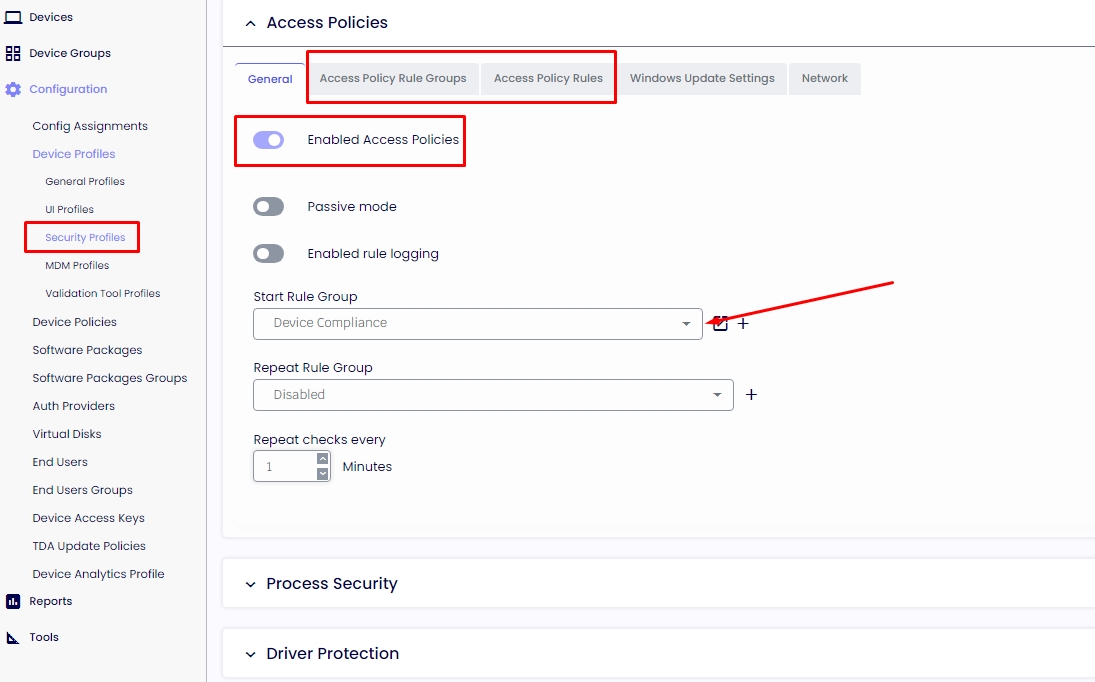
Our Access Policies does a pre-check before launching the session with conditions selected from “Access Policy Rules."
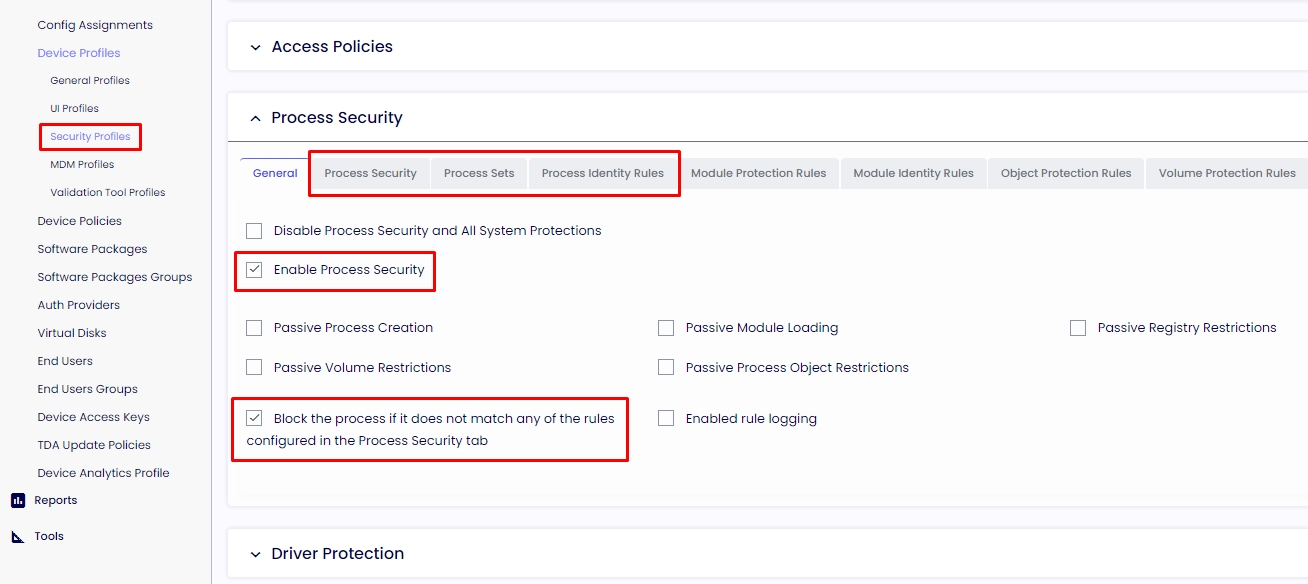
Process Identity is one of the most important functions in the profile and a critical component of the ThinScale security features set. Applications will be allowed once verified by signed security certificates, file description, file hash, and other methods, which give a very high level of protection against running any other apps than the ones you have defined. In other words, every process is blocked in the background of the session if not allowed in the Process Security section. By default, we only whitelist the minimum Windows services required to run our application and the applications you selected on the Quick-Start.
Should you require assistance with your product, a wealth of information is available to help you find the answers you need. Please refer to the following resources:
Device Portal Knowledge Base
Device Portal Admin Guide
ThinScale Academy
These resources contain comprehensive information and instructions on using and troubleshooting our product. If you cannot find the information you need after consulting these resources, please don't hesitate to contact our support team for further assistance.